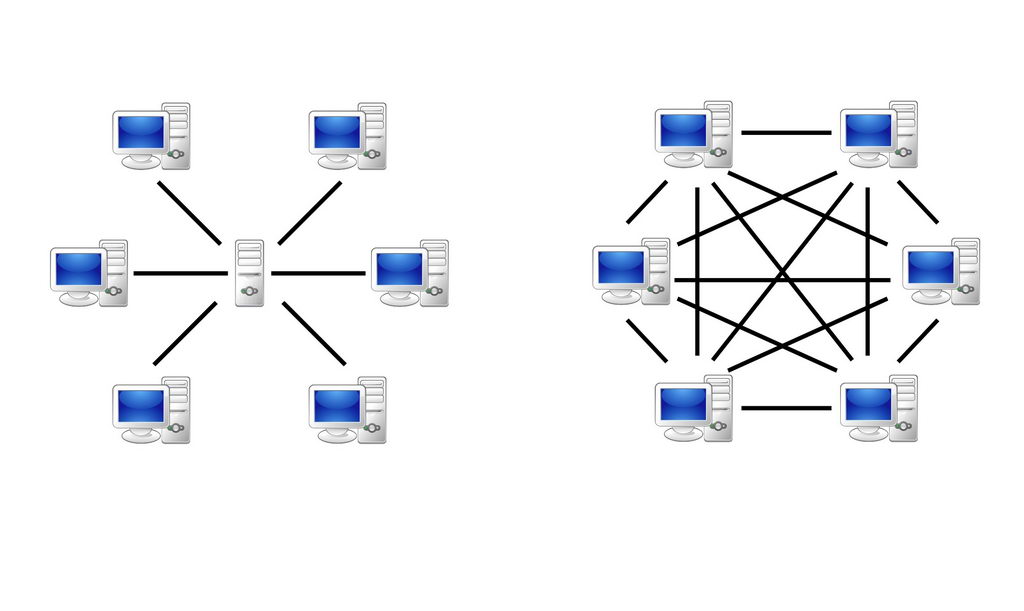
5 Tips for Protecting Your Small Business from Cyber-Hackers
5 Tips for Protecting Your Small Business from Cyber-Hackers
1) Commercial Grade Antivirus
Gone are the days when free, downloadable antivirus software could keep your business safe from outside threats. In our new age of increasing cyber vulnerability, you need hardy software to protect the business you’ve worked so hard to grow.
While there are many free antivirus software options, they all share some common, massive vulnerabilities: features and updates. Free software lacks the range of features that protect you from different infection sources: email, web, network, etc. Plus, many only update once per week, and there’s a whole slew of malicious things that can happen between these updates. Business grade antiviruses update several times a day, and they are much more complete and secure. Even better, most only cost about $35 per device per year!
This is one area where you can’t afford to opt for the free version. With devastating viruses like WannaCry! becoming more and more common, the primary line of defense for small businesses is a strong antivirus.
Here are our top picks: ESET Endpoint Security and Symantec Antivirus
2) VPN Routers or Firewall Appliances
Handling sensitive records and client information? Need an actually secure way to remote in from home to your business computers? If so, a VPN Routers or Firewall Appliances are a must.
Firewall appliances keep connections safe and secure from hacking and other cyber-attacks. Is your business HIPPA compliant? HIPPA compliant firewall routers are even more secure and they are required if your business falls under HIPPA standards.
Lastly, VPN Routers or Firewall Appliances give you the ability to securely remote in to your business computers from home. Don’t feel like going into the office? Or, need to access sensitive client information while you’re on a business trip? VPN and firewall routers make it safe to access your business data from anywhere.
Here are our favorites: Cisco Small Business VPN Routers and Sophos Firewalls
3) Regular Maintenance and Updates
For some, this is a no-brainer. For others, it simply never happens. Whichever category you fall into, it can still be challenging to keep regular, scheduled maintenance and updates a priority. Regardless, doing regular maintenance on your business computers and network is critical to maintaining your security, fast access to data, and a trouble-free work experience.
Regular software updates for Windows, Java, Antiviruses and other software help keep your computers safe and secure. Just as important, backups should be checked routinely to make sure they are working properly. There is nothing that can ruin your day like needing to retrieve a backup to find out it is not there, incomplete, or corrupted.
This is by far the easiest security component to neglect, but it is also one of the most dangerous. Which is why, for many, it is extremely prudent to hire someone to do it for you. An IT company can help enormously by using automated remote monitoring software. This will guarantee that updates are routinely done and hard drives/data backups are monitored for defects so they can be replaced before they fail and you lose critical data.
Are you in the Carolinas? CDO Technologies provides just these services for local businesses. Learn more here.
4) Trusted Back-Ups
If you have data that is critical to the daily operation of your business, you know how scary the thought of losing that data is. Accordingly, it is essential that you have consistent backups you can trust.
To insure against the worst, you need an on-premise backup and a Cloud backup. The on-premise backup allows you to quickly retrieve critical information if your computer or server’s hard drives die, files are damaged, or files and folders are lost.
On the other hand, the Cloud backup allows you retrieve your critical data if the worst happens. Your office could be flooded or a fire could destroy the computer or server that critical data is on. Somebody could steal the computer or backup that has critical data on it or a nasty virus could infect all your office’s hard drives/backups with critical data on them. These scenarios may sound farfetched, but they happen to businesses every day. Cloud Backups store older versions of the backup (perhaps only days before the infection) that have not been infected yet. Using Cloud backups, you can reset to happier times and get back to work.
5) Annual Network Evaluation
Five years ago, you invested in new network infrastructure. At first everything worked great, but slowly you began demanding more. As the number of employees grew, new and beefier software was added to your daily business operations. You asked for your IT infrastructure to do more and different types of work with the same equipment. And, finally, the obsolescence of your (now dated) computers, network equipment, and servers set in and caused slowness, lockups, and employee aggravation.
The tech world is moving faster every day, and you are responsible for keeping up. Your network infrastructure has to be maintained and eventually upgraded to keep up with a growing business. Otherwise, you will inevitably fall in a tangled heap of inefficiencies, security holes, frustration, and pain.
To protect against this failure, get your network evaluated annually by IT professionals.
Are you in the Carolinas? CDO Technologies provides just these services for local businesses. Learn more here.